SEE EVERYTHING.
PREDICT WHAT MATTERS. MANAGED IN THE CLOUD.
The visualization, analytics and measurement solution to transform vulnerability data into meaningful insights.

Support the company’s marketing activity, ranging from effective sales tracking to prospect management, with one centralized system.
With coverage for more than 72,000 vulnerabilities, Z Square has the industry’s most extensive CVE and security configuration support to help you understand all of your exposures.
Combine vulnerability data, threat intelligence, and data science for easy-to-understand risk scores to quickly assess risk and know which vulnerabilities to fix first.

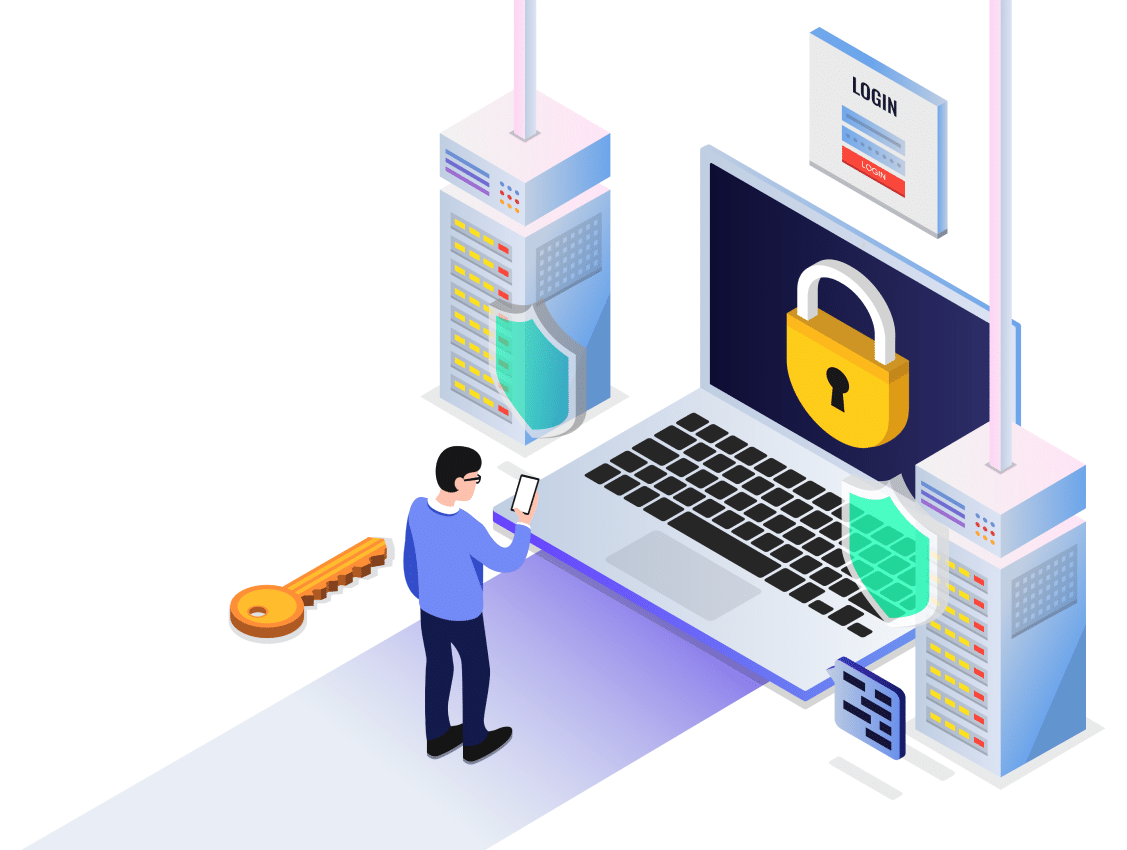
GET CLOUD-BASED VULNERABILITY MANAGEMENT FOR COMPLETE VISIBILITY INTO THE ASSETS AND VULNERABILITIES IN YOUR ORGANIZATION.
A diverse array of sensors automatically gathers and analyzes your security and vulnerability data. You get full visibility into your entire attack surface - for any asset on any computing platform.
Continuously track and assess known and unknown assets and their vulnerabilities—even highly dynamic IT assets like mobile devices, virtual machines, containers, and cloud instances.
Proactively identify and prioritize vulnerabilities with the highest impact on your organization. Get targeted alerts when new threats appear to quickly respond.
Get immediate insight with intuitive dashboard visualizations for rapid analysis. Customize reports to inform security teams about critical issues.
Cybersecurity, often spelled as “cyber security,” is the practice of protecting computer systems, networks, and digital data from theft, damage, unauthorized access, or other malicious activities. It encompasses a wide range of strategies, technologies, and practices designed to safeguard sensitive information, maintain the integrity and availability of digital systems, and protect against cyber threats. These threats can include viruses, malware, phishing, hacking, data breaches, and more. Cybersecurity measures are crucial in our increasingly digitized world to ensure the confidentiality, integrity, and availability of data and to minimize risks to individuals, organizations, and governments.
Data Protection: Cybersecurity is primarily used to protect sensitive data from theft, unauthorized access, and breaches, ensuring the confidentiality and integrity of information.
Defense Against Cyber Threats: It safeguards digital systems and networks from malware, cyberattacks, and other malicious activities that could disrupt operations, compromise security, or lead to financial losses.
Resilience and Continuity: Cybersecurity measures also help organizations maintain business continuity, ensuring that systems remain available and functional in the face of cyber incidents or disasters.
Protection of Sensitive Data: Cybersecurity safeguards sensitive information, preventing data breaches and unauthorized access, which can lead to financial losses and damage to reputation.
Business Continuity: It ensures the uninterrupted operation of digital systems and networks, minimizing downtime and preventing disruptions caused by cyber incidents, ultimately saving time and resources.
User Trust: Strong cybersecurity builds trust among customers, partners, and stakeholders, demonstrating a commitment to data protection and privacy, which can enhance an organization's reputation and competitiveness.
Copyright © 2023 Z Square Solutions. All Rights Reserved.
WhatsApp us